 How much do you know about the hacking collective Anonymous? Many
people have assumptions about the mysterious group of hackers.
Proponents of the group say that Anonymous is fighting the people's
fight, standing up for issues they believe that governments and large
corporations ignore by hacking websites and sending distributed denial
of service (DDoS) attacks.
How much do you know about the hacking collective Anonymous? Many
people have assumptions about the mysterious group of hackers.
Proponents of the group say that Anonymous is fighting the people's
fight, standing up for issues they believe that governments and large
corporations ignore by hacking websites and sending distributed denial
of service (DDoS) attacks.On the other hand, critics see group as a bunch of teenagers who sit around in hoodies trolling others and causing mayhem just for the "lulz" (entertainment).
With such a huge, decentralised global online network of hacktivists, it's sometimes difficult to truly put your finger on what Anonymous is trying to achieve from their activities. Although some cyberattacks seem to have a clear purpose, others could just be publicity stunts or for the general merriment of the group, rather than for the greater good or some higher purpose.
But one group of operatives, who call themselves the Ghost Security Group, know exactly what they are trying to achieve, and have even broken away from Anonymous in order to further legitimise their work, which is to track the activities of Islamic State (Isis) online and prevent potential terrorist attacks.
Moving away from DDoS-ing websites
"In January 2015, after the Charlie Hebdo shootings in Paris, we were DDoS-ing websites heavily and we took down about 180 jihadist websites as GhostSec in Anonymous. That's when we realised that DDoS-ing was not the only thing we could do, and we assisted authorities in stopping an impending attack. Sometimes when you watch people and use that information against them, it leads to you being able to save actual human lives and we feel that that's far more effective than DDoS-ing."
So Digitashadow and a group of hacktivists from Anonymous' GhostSec decided to break away from the hacking collective in May 2015 and move towards legitimacy, forming the non-profit organisation Ghost Security Group (GSG), which primarily analyses data from IS-related social media accounts on platforms like Twitter and the encrypted messaging platform Telegram, and passes on important bits of information straight to relevant US intelligence agencies.
"We saw that with Islamic State, for the first time, this issue wasn't restricted to the Middle East. They could attack people in London, Paris, the US. We felt not enough was being done and it was a wake-up call for a lot of us to try to do something, to bring the fight back to them," Digitashadow explains.
"We don't want to be a rogue hacker group, we wanted to move more towards legitimacy. Anonymous weren't happy about us stepping away but it had to be done. We can't make arrests, we don't have guns or boots on the ground, so in order to get [the job] done we had to move closer to the government."
Gathering intelligence to stop imminent terrorist attacks
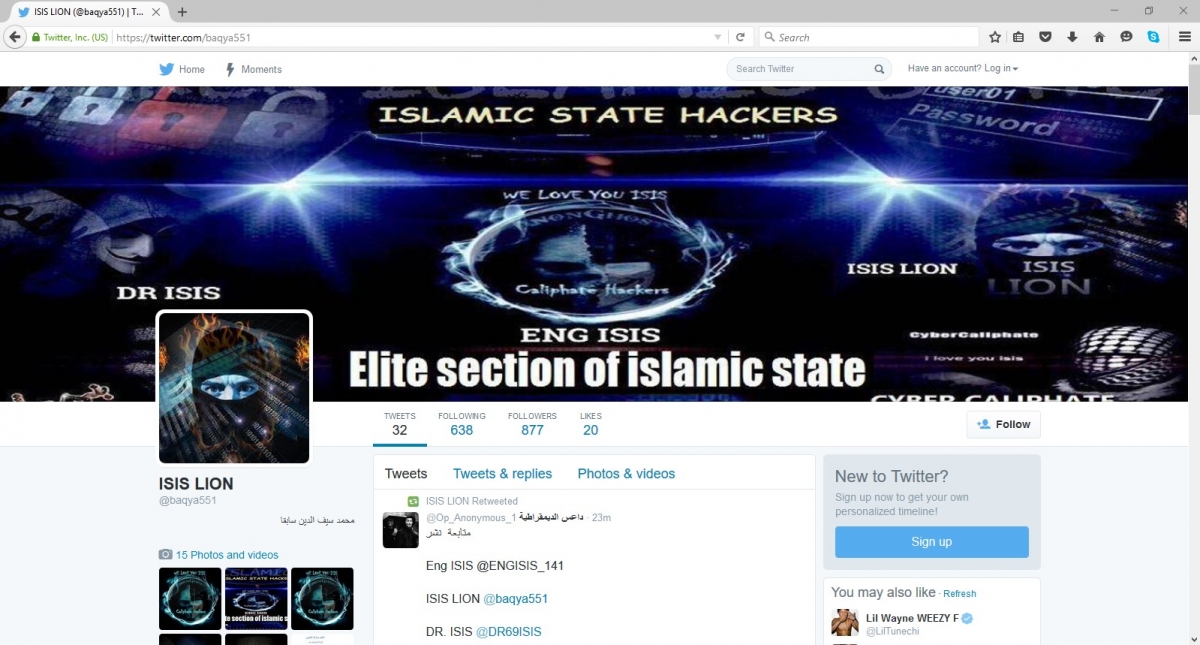
For the first objective, the group reports accounts and links to relevant service providers, and in one year, GSG has taken down 120,000 Twitter accounts and 7,000 propaganda videos hosted on Google Drive, Microsoft One Drive, YouSendit, Archive.org, YouTube, Facebook and Twitter. On average, the group also submits between 3,000-5,000 IS-related account usernames a month to Twitter to ban.
But the second objective is trickier – how does a civilian bypass multiple levels of bureaucracy to get crucial information to the right authorities, and which intelligence agency, out of the many in the US, is the right one?
To begin with, GSG targeted channels open to the public, like the FBI tips hotline, but they soon realised that the information wasn't getting anywhere near decision-makers in time, if at all. So Digitashadow and his 16 colleagues sought help from Michael S Smith II, a terrorism analyst and co-founder of Kronos Advisory who is currently serving as a contributing expert to the US Congressional Task Force on Terrorism and Unconventional Warfare.
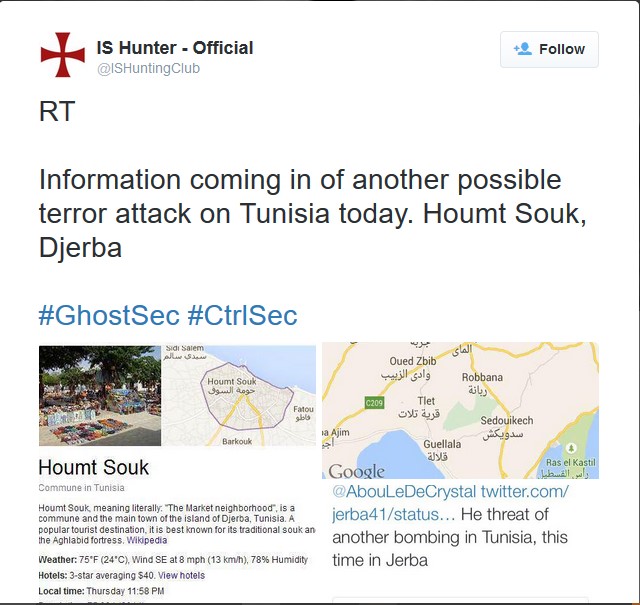
"They presented information to me about a potential attack plot in Tunisia gathered from key figures in an Islamic State-linked social media network, and since then they have given me data identifying accounts and servers, pointing to the most aggressive and effective influence operation of any terrorist group in history."
Through his work, Smith has amassed many contacts who are high-ranking officials in multiple intelligence agencies in the US, and he quickly realised that the best way to get the right people in the US government to quickly act on the GSG's data was to send it to them all, as the intelligence agencies rarely co-operate with each other to share information, and the FBI tips hotline is inundated with far too much information.
"Digitashadow is providing a lot of useful information to help improve understanding of Islamic State and he's doing this without receiving compensation. US officials are comfortable with receiving information from GSG. They have confidence in the quality and integrity of their information, because officials can promptly look at social media accounts and verify that the statements are true," stresses Smith.
"The fact that Digitashadow is not under contract, that there is no formal arrangement between him and one intelligence agency, means his information can be shared with all the agencies. The FBI is inundated with tons of information on their hotline, everything from jokes about UFO sightings to al-Qaeda leaders sighted playing slots in Las Vegas. If you have time-sensitive information, the best way to get that data into officials' hands is to contact them directly."
Comparisons with Anonymous

"We're an intelligence-collecting platform. Anonymous likes to attack heavily, we're not aggressive, we'd rather collect data and find a way to use it against them. Second, we have an organisation-based leadership. Anonymous is decentralised. That's kinda the reason we left as everyone just does what they want, but no one knows what anyone else is doing. We have leadership and structure," explains Digitashadow.
"Also, Anonymous doesn't have the level of seriousness. There's been cases where we have stopped attacks, but meanwhile they've been busy trolling Isis with a music video. Yeah, five to 10 years ago I would have done that too, but part of it is growing up."
Digitashadow also emphasises that he and his colleagues do work that Anonymous would find boring, such as creating endless fake IS supporter accounts, letting them get suspended by Twitter and retweeting propaganda to gain credibility and then talking to IS-related social media accounts that appear to be terrorists for months on end in the hopes that terrorists will feel comfortable enough to ask GSG about the potential of conducting terrorist attacks in the US.
"We don't engage them directly; we wait for them to come to us. We have had actual militants contact our infiltrators who are in the US, and the militants ask us about conducting an attack in the US, and we screenshot everything. If they're pushing an attack, then we will send the information off to Mr Smith immediately," says Digitashadow. "We've stopped five attempts in the last year."
Doing it all for free
"It's been very exciting to see how dedicated this group of people is to providing support to the counter-terorism community. Particularly when some complacencies have resulted in these individuals not being compensated for a great deal of valuable work," says Smith.
"While they recognise the US goverment is at the tip of the spear in the fight against IS, which is why they're not offering their services to any of the many governments who would put them under contract and pay them handsomely, I think GSG doesn't particularly want government jobs.
"They are keenly aware of the possibility of government databases being hacked, so information about them would be exposed. IS has built out a pool of supporters who have the capabilities of breaching government data, and they would love to know who GSG are."
Digitashadow told us he works 16-17 hours a day, seven days a week, but he receives no financial compensation either, surviving only on the donations sent to the group by well-wishers. The group also routinely receives death threats from IS, but he doesn't seem to mind.
He said: "I came from an IT background and there are times that I do think about the fact that other people in the IT industry are making loads of money and have a much better life than me, but we're saving lives. Even if we've only saved one life this last year, this entire time was worth it."
ibtimes