More than 6 months after its creator was sentenced to prison, the infamous Citadel malware resurges in a modified form, called Atmos. The new strain is currently targeting banks in France and it was also spotted being delivered with Teslacrypt. Here’s the full story.
Citadel emerged in 2011, when cyber criminals used the leaked ZeuS code to create new and advanced malware strains that could do more harm while going undetected for longer. The banking Trojan soon became a type of malware distributed at a massive scale, as shown in this FBI press release issued when Citadel’s maker was convicted:
Citadel was not only capable of stealing money, but also personal data. The huge botnet behind it gave it the power to execute code on the enslaved computers, infecting them with malware from scareware to ransomware.
The malicious actors behind Citadel then started to target public and private organizations, especially located in Europe, harvesting credentials to access internal applications and information management systems.
On June 5 2013, the Microsoft Digital Crimes Unit announced that it was working with the FBI and other law enforcement agencies to break off and block the cyber crime ring behind Citadel and its activity.
From ZeuS to Citadel to Atmos – the years may have passed, but cyber criminals are not ready to give up on using the source code it all began with. In fact, this new Citadel variant that researchers have analyzed is modified sufficiently for it to have a new name. That’s why Malwarebytes dubbed it “Atmos” when they first came across it.
So far, only a few strains of Atmos have been detected and what they have in common is attacks targeting banks in France. Because it’s based on Citadel, which, in turn, evolved from ZeuS, Atmos utilizes the same web injects that ZeuS became infamous for. Consequently, we can infer that this new financial malware strain is after the same objectives: money and confidential data.
Recent samples that have been analyzed are downloading encrypted “configs” from the following malicious URLs:
http://caras1tycu4tion[.]com/aksasdfw1qizjxnhquw/f-asdhqwdjauqo.php
http://stata55worldosmat[.]info/aksasdfw1qizjxnhquw/f-asdhqwdjauqo.php
http://opahdiqwqweqkweklnasd[.]com/aksasdfw1qizjxnhquw/f-asdhqwdjauqo.php
The latest Control & Command / config servers for Atmos are located in Vietnam, Canada, Ukraine, Russia, the US and Turkey. There are almost 1000 bots already recruited in the network,
but the number may increase as a result of recent attacks.
Consequently, compromise attempts can become increasingly powerful or
the attackers can focus their actions on bigger, more attractive
targets.
Here is a list of Indicators of Compromise tied to the new Atmos Trojan:
http://iguana58[.]ru/plugins/system/anticopy/adobe[.]exe
http://tehnoart[.]co/sr[.]exe
http://3dmaxkursum[.]net/tmp/sys/config[.]exe
http://iguana58[.]ru/plugins/system/anticopy/adobe[.]exe
http://mareikes[.]com/wp-includes/pomo/svhost[.]exe
http://mareikes[.]com/wp-includes/pomo/server[.]exe
In an interesting development, Atmos was observed being delivered with Teslacrypt, whose latest variant (TeslaCrypt 4) features unbreakable encryption and enhanced data-stealing capabilities.
The analysis also showed that there is at least one group of cyber criminals who is using Atmos in its attacks, so the new banking Trojan remains under observation.
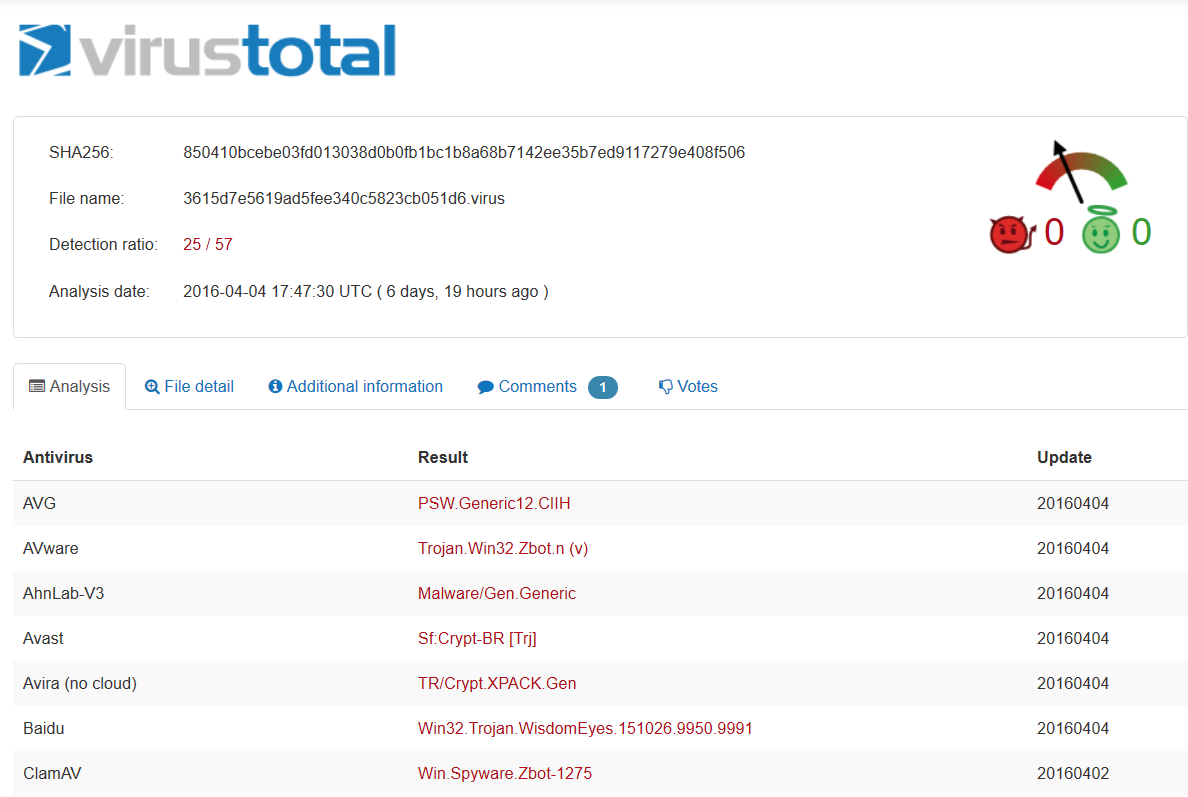
The good news is that antivirus detection is quite good, scoring 25/57 according to VirusTotal:
Banking Trojans haven’t been as active as ransomware strains in the past half a year, but there’s nothing stopping them from making a comeback. And this is especially the case since users and companies tends to expose themselves to cyber attacks for lack of adequate patching.
* This article features cyber intelligence provided by CSIS Security Group researchers.
heimdalsecurity
Quick background
Citadel emerged in 2011, when cyber criminals used the leaked ZeuS code to create new and advanced malware strains that could do more harm while going undetected for longer. The banking Trojan soon became a type of malware distributed at a massive scale, as shown in this FBI press release issued when Citadel’s maker was convicted:
Dimitry Belorossov, a/k/a Rainerfox, has been sentenced to four years, six months in prison following his guilty plea for conspiring to commit computer fraud. Belorossov distributed and installed Citadel, a sophisticated malware that infected over 11 million computers worldwide, onto victim computers using a variety of infection methods.
In 2012, Belorossov downloaded a version of Citadel, which he then used to operate a Citadel botnet primarily from Russia. Belorossov remotely controlled over 7,000 victim bots, including at least one infected computer system with an IP address resolving to the Northern District of Georgia. Belorossov’s Citadel botnet contained personal information from the infected victim computers, including online banking credentials for U.S.-based financial institutions with federally insured deposits, credit card information, and other personally identifying information.Source: FBI press release
Citadel was not only capable of stealing money, but also personal data. The huge botnet behind it gave it the power to execute code on the enslaved computers, infecting them with malware from scareware to ransomware.
The malicious actors behind Citadel then started to target public and private organizations, especially located in Europe, harvesting credentials to access internal applications and information management systems.
The Zeus malware platform was originally designed to steal currency, frequently in small amounts from thousands of victims. Citadel’s developers, however, have clearly recognized that sometimes data, particularly authentication credential data, can be more valuable than currency. Consequently, in the second half of 2012 we began to see Citadel variants designed to penetrate local government and large private enterprise IT infrastructure.Source: McAfee Labs, Inside the World of the Citadel Trojan Executive Summary
On June 5 2013, the Microsoft Digital Crimes Unit announced that it was working with the FBI and other law enforcement agencies to break off and block the cyber crime ring behind Citadel and its activity.
With a court ordered civil seizure warrant from the U.S. District Court for the Western District of North Carolina, Microsoft executed a simultaneous operation to disrupt more than 1,400 Citadel botnets which are responsible for over half a billion dollars in losses to people and businesses worldwide.Source: The Official Microsoft Blog
Atmos – Citadel’s polymorphic successor
From ZeuS to Citadel to Atmos – the years may have passed, but cyber criminals are not ready to give up on using the source code it all began with. In fact, this new Citadel variant that researchers have analyzed is modified sufficiently for it to have a new name. That’s why Malwarebytes dubbed it “Atmos” when they first came across it.
So far, only a few strains of Atmos have been detected and what they have in common is attacks targeting banks in France. Because it’s based on Citadel, which, in turn, evolved from ZeuS, Atmos utilizes the same web injects that ZeuS became infamous for. Consequently, we can infer that this new financial malware strain is after the same objectives: money and confidential data.
Recent samples that have been analyzed are downloading encrypted “configs” from the following malicious URLs:
http://caras1tycu4tion[.]com/aksasdfw1qizjxnhquw/f-asdhqwdjauqo.php
http://stata55worldosmat[.]info/aksasdfw1qizjxnhquw/f-asdhqwdjauqo.php
http://opahdiqwqweqkweklnasd[.]com/aksasdfw1qizjxnhquw/f-asdhqwdjauqo.php
Atmos has been active since late 2015, but has only recently surged in activity.
Here is a list of Indicators of Compromise tied to the new Atmos Trojan:
http://iguana58[.]ru/plugins/system/anticopy/adobe[.]exe
http://tehnoart[.]co/sr[.]exe
http://3dmaxkursum[.]net/tmp/sys/config[.]exe
http://iguana58[.]ru/plugins/system/anticopy/adobe[.]exe
http://mareikes[.]com/wp-includes/pomo/svhost[.]exe
http://mareikes[.]com/wp-includes/pomo/server[.]exe
In an interesting development, Atmos was observed being delivered with Teslacrypt, whose latest variant (TeslaCrypt 4) features unbreakable encryption and enhanced data-stealing capabilities.
The analysis also showed that there is at least one group of cyber criminals who is using Atmos in its attacks, so the new banking Trojan remains under observation.
The good news is that antivirus detection is quite good, scoring 25/57 according to VirusTotal:

Conclusion
If Citadel was one of the top 10 most dangerous financial malware that can infect your system, we ca only assume that Atmos is a similarly powerful threat.Banking Trojans haven’t been as active as ransomware strains in the past half a year, but there’s nothing stopping them from making a comeback. And this is especially the case since users and companies tends to expose themselves to cyber attacks for lack of adequate patching.
* This article features cyber intelligence provided by CSIS Security Group researchers.
heimdalsecurity