Ransomware attacks have grown exponentially in 2015, and all evidence points to the fact that the trend is likely to continue. In the UK alone, 42% of security breaches were caused by ransomware attacks.
In this context, our team has recently discovered an aggressive spam campaign that hooks victims with a fake invoice or order. Although this technique is not new and cyber security specialists have warned about it repeatedly (our team included), it still results in massive revenue for attackers.
In this campaign, the email includes an invoice that supposedly comes from Salesforce, a reputed company from the US which offers a customer relationship product used in companies around the world.
The contents of the unsolicited email include a semi-dynamic subject line and an attached .doc file:
From: [spoofed / fake return address]
Subject line: (more combinations like the ones below)
salesforce – Billing Statement Overdue [% name of the receiver%] salesforce.com – Contract Confirmation of [% name of the receiver%] [% name of the receiver%] Your Telephone Bill Report is due
[% name of the receiver%] Your Phone and Data Billing Report is due
www.salesforce.com Order Confirmation for
Attached: [% name of the receiver%] _ Contract.doc
The attached .doc file conceals a deceptive macro, which, if activated, will download the CryptoWall 4.0 payload from the following URL:
http: // mastfm102 [.] com / wordpress / wp-includes / asalam.exe
The malicious Cryptowall 4.0 variant is then copied on the victim’s system, in the following location:[% user account%] \ AppData \ Local \ Temp \ VBE \ MSForms.exe
In the next stage, the payload will connect to a long list of compromised web servers where the victim’s data will be exfiltrated to. Here a segment of this list that includes some of the servers currently controlled by the attackers behind this campaign:
http://thebeautythesis[.]com/UaEigq.php
http://thebesttshirtsonline[.]com/CF9iM8.php
http://turbosol[.]asia/l7xydO.php
http://uzmankirala[.]com/KhVRbv.php
http://vancouverdispensarycoalition[.]ca/euqUb5.php
http://villisplace[.]info/fJQ_3v.php
http://vinastudio[.]at/8TkXUJ.php
http://wallpapersau[.]net/igrHKY.php
http://yardstickglobal[.]in/Y37Jux.php
http://zolty[.]eu/bnFKET.php
The malicious code reveals that the campaign uses the following ID: “crypt5029”.
As it generally happens with ransomware campaigns, antivirus detection is very low, as you can see from this example:
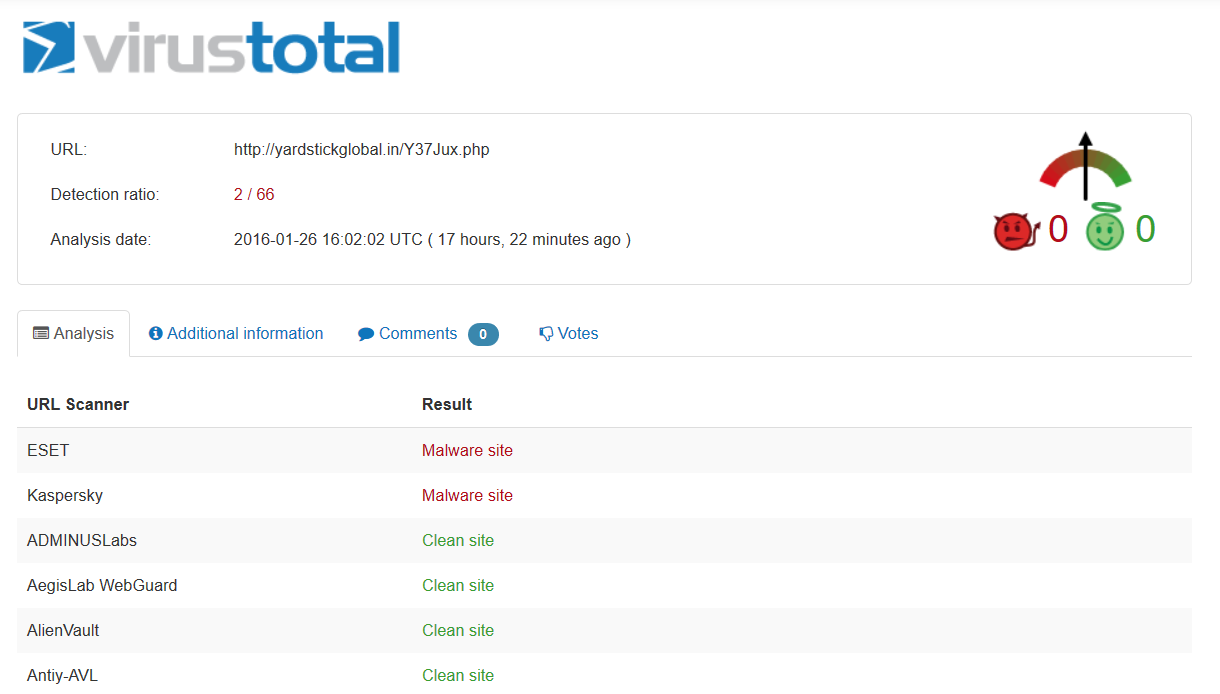
Check out the full detection rates for one of the infected web servers in the list above, specifically http://yardstickglobal[.]in/Y37Jux.php, on VirusTotal.
Ever since we announced that CryptoWall 4.0 surfaced in November 2015, we’ve seen Angler become an important part of the mix, which caused millions in losses for those that fell victims to it.
Companies, especially small and medium ones, are attractive targets for cyber criminals, because they:
tend to favour a BYOD environment, where personal devices are also used to run the business;
store and manage attractive data, such as customer contact information, credit card data, health data, intellectual property and more;
tend to be less secure, because they cannot afford sophisticated cyber security technologies, which means that cyber criminals can easily find vulnerabilities they can exploit to get into the PCs or network;
lack the time, budget and expertise needed to build a strong security system to protect business assets (this includes the lack of an in-house cyber security specialist);
can be attacked via automated attacks – cyber criminals employ readily accessible malware kits to mass produce attacks with little investments; these attacks are automated and the attackers don’t care who they hit, as long as they get what they want;
don’t usually conduct employee training and don’t do risk assessments;
sometimes outsource cyber security tasks to unqualified service providers;
are much more interconnected than have ever been, with a mix of PCs (desktops, laptops), smartphones and cloud-store data to safely manage and protect, which is not always easy to do;
can be used as stepping stones to gain access into bigger targets, as small and medium business often act like service providers to big companies, which are more lucrative targets for cyber criminals.
If we stop to analyze the evolution of CryptoWall and its strains, we’ll see that each strain lasted for a few months until an enhanced, stealthier strain surfaced.
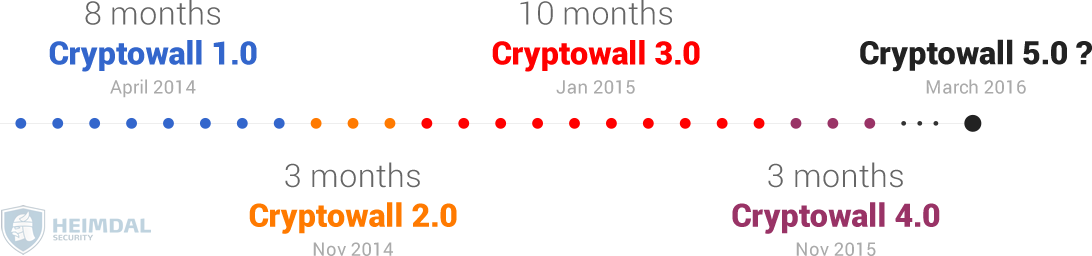
To date, CryptoWall 3.0 was the longest lasting strain on the market, but CryptoWall 4.0 came with vastly improved communication capabilities and an increased ability to stay under the radar, so there’s no telling how long it will last.
However, we can assume that CryptoWall 5.0 is around the corner and could emerge in the next 3 months. While we cannot precisely anticipate its features, we can prepare with adequate protection.
Companies of any size shouldn’t postpone implementing basic security measures to keep their data protected. Automatic patching, enabling macro protection, doing employee training – they are all solutions that are bothaffordable and effective.
A ransomware infection can have daunting effects on any business, and a huge part of the risk can be mitigated through basic cyber security measures. Acting today will give you peace of mind and a better outlook on tomorrow.
https://heimdalsecurity.com/blog/new-cryptowall-4-0-campaign-preparation-cryptowall-5-0/?utm_source=Heimdal+Security+Newsletter+List&utm_campaign=6e65c51461-RSS_Newsletter&utm_medium=email&utm_term=0_31fbbb3dbf-6e65c51461-196325841&goal=0_31fbbb3dbf-6e65c51461-196325841